Difference between revisions of "DEP Boot.ini Considerations"
Jump to navigation
Jump to search
Troy.Forcier (talk | contribs) m |
|||
| (2 intermediate revisions by 2 users not shown) | |||
| Line 4: | Line 4: | ||
This option is only available with '''32-bit''' versions of Windows and on processors capable of ''no-execute protection''. It enables no-execute protection (aka Data Execution Protection - DEP), which results in the Memory Manager defining pages containing data as ''no-execute'' so that they cannot be executed as code. | This option is only available with '''32-bit''' versions of Windows and on processors capable of ''no-execute protection''. It enables no-execute protection (aka Data Execution Protection - DEP), which results in the Memory Manager defining pages containing data as ''no-execute'' so that they cannot be executed as code. | ||
This can be useful for stoping malicious code from taking advantage of buffer overflow flaws with unexpected program input in order to execute arbitrary code. | This can be useful for stoping malicious code from taking advantage of buffer overflow flaws with unexpected program input in order to execute arbitrary code. | ||
| + | |||
| + | More info in [http://support.microsoft.com/kb/875352 MS KB] | ||
:''Note'': No-execute protection is always enabled on '''64-bit''' versions of Windows on processors that support no-execute protection. | :''Note'': No-execute protection is always enabled on '''64-bit''' versions of Windows on processors that support no-execute protection. | ||
| Line 12: | Line 14: | ||
* '''/NOEXECUTE=ALWAYSON''': Enables DEP on all images. | * '''/NOEXECUTE=ALWAYSON''': Enables DEP on all images. | ||
* '''/NOEXECUTE=ALWAYSOFF''': Disables DEP. | * '''/NOEXECUTE=ALWAYSOFF''': Disables DEP. | ||
| + | |||
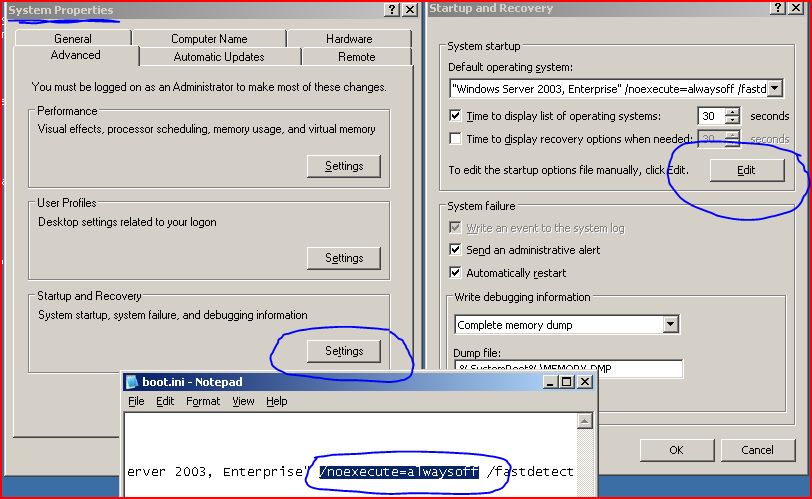
| + | [[Image:EditBootini.jpg]] | ||
Latest revision as of 16:11, 27 August 2008
/NOEXECUTE
One of a number of Boot.ini switches that are useful for testing a variety of system settings without having to have a different machine for each one.
This option is only available with 32-bit versions of Windows and on processors capable of no-execute protection. It enables no-execute protection (aka Data Execution Protection - DEP), which results in the Memory Manager defining pages containing data as no-execute so that they cannot be executed as code. This can be useful for stoping malicious code from taking advantage of buffer overflow flaws with unexpected program input in order to execute arbitrary code.
More info in MS KB
- Note: No-execute protection is always enabled on 64-bit versions of Windows on processors that support no-execute protection.
Options
There are several options you can specify with this switch:
- /NOEXECUTE=OPTIN: Enables DEP for core system images and those specified in the DEP configuration dialog.
- /NOEXECUTE=OPTOUT: Enables DEP for all images except those specified in the DEP configuration dialog.
- /NOEXECUTE=ALWAYSON: Enables DEP on all images.
- /NOEXECUTE=ALWAYSOFF: Disables DEP.